Cyber criminals affected the online businesses and individuals since the internet networks first appeared and spread all over the world.
Internet services and websites make it easy for us to pay bills, shop, make online reservations and even work. And you can do any of these actions from any place in the world. Old boundaries and human limitations were dropped, in order for us to have access to almost any information. Our lives became so much easier.
But the same thing is true for CRIME.
Our freedom to navigate and access a wide number of online locations represents in the same time a main vulnerability, because an open door always allows access in both directions.
Criminal minds can reach these days further than before, into our private lives, our homes and work offices. And there is little we can do about it.
Attack methods and tools vary from traditional attack vectors, which use malicious software and vulnerabilities present in almost all the programs and apps (even in the popular Windows operating systems), to ingenious phishing scams deployed from unexpected regions of the world, where justice can’t easily reach out to catch the eventual perpetrators.
The most common ways for you to become vulnerable to a malware attack orphishing scam take place when you:
- shop online
- check your email
- access social media networks
For this reason, we need to know what are the most popular schemes and techniques used by cyber criminals in order to obtain our private information and financial data.
We must not forget their final target is always our money and there is nothing they won’t do to accomplish their mission.
1. Phishing email scams
Phishing scams are based on communication made via email or on social networks. Cyber criminals will send you messages and try to trick you into giving them your login credentials – from your bank account, social network, work account, cloud storage or any other personal data that can prove to be valuable for them.
In order to do that, the phishing emails will seem to come from an official source – it can be bank authorities or other financial institutes, but also delivery companies or social networks representatives.
This way, they’ll persuade you to click on the links contained by their messages and access a website that looks legit, looks like the real one, but it’s actually controlled by them. You will be sent to a fake login access page that resembles the real website.
This way, if you’re not paying attention, you might end up giving your login credentials and other personal information.
In order for their success rate to grow, scammers create a sense of urgency. They’ll tell you a frightening story of how your bank account is under threat and how you really need to access as soon as possible a web page where your must insert your credentials in order to confirm your identity or your account.
Of course, the provided link will only lead you to the fake web location and not to the real login page.
After you fill in your online banking credentials, cyber criminals use them to breach your real bank account or to sell them on the dark web to other interested parties.
It’s one of the main scamming techniques used to spread financial and data stealing malware. There isn’t any reason why you shouldn’t be very well prepared for this attempt. However, even if you install a good antivirus program, there is no better way to stay safe from this threat but to avoid the initial infection phase.
Here’s a complete guide on how to detect and prevent phishing attacks – filled with screenshots and actionable tips.
2. The money laundering scam
This money laundering scam – also known as the Nigerian scam – is actually one of the oldest and most popular scamming schemes. Most of us already encountered it in our own email inbox, in one form or another.
Since it’s an old scam, it suffered multiple variations along the years.
The typical scam starts with an emotional email message. It can be from an official government member, a businessman or a member of a very wealthy family member (usually a woman) who asks you to provide help in retrieving a large sum of money from a bank, paying initially small fees for papers and legal matters. In exchange for your help, they promise you a very large sum of money.
Of course, this is just the beginning. Afterwards, they ask you to pay more and more for additional services, such as transactions or transfer costs. You even receive papers that are supposed to make you believe that it’s all for real. In the end, you are left broke and without any of the promised money.
There were also cases where not only money was lost in the scam, but people were kidnapped or even worse.
In this blog post we exposed more examples of scams carried on social media networks (tips on how to stay safe from them included).
3. Greeting card scams

This is another old scam: the greeting cards that you receive in your email inbox and seem to be coming from a friend.
If you open such an email and click on the card, you usually end up with malicious software that is being downloaded and installed on your operating system.
The malware may be an annoying program that will launch pop-ups with ads, unexpected windows all over the screen. However, it can also be ransomware or one of the worst financial malware that’s been around, part of the infamous Zeus family.
If your system becomes infected with such dangerous malware, you will become one of the bots which are part of a larger network of affected computers. In this unfortunate event, your computer will start sending private data and financial information to a fraudulent server controlled by IT criminals.
To keep yourself safe from identity theft and data breach, we recommend using a specialized security program against this type of dangers.
To find out more information about financial malware, read this article.
4. A guaranteed bank loan or credit card scam

Difficult times push people into getting trapped by “too good to be true” bank offers that guarantee you large amounts of money and have already been pre-approved by the bank.
If such an incredible pre-approved loan is offered to you, simply use your common sense to judge if it’s for real or not.
How is it possible for a bank to offer you such a large sum of money without even knowing your financial situation?
Though it may seem unlikely for people to get trapped by this scam, there’s still a big number of people who lost money by paying the “mandatory” processing fees required by the scammers.
Here are more tips and tricks from top security experts:
5. Lottery scam
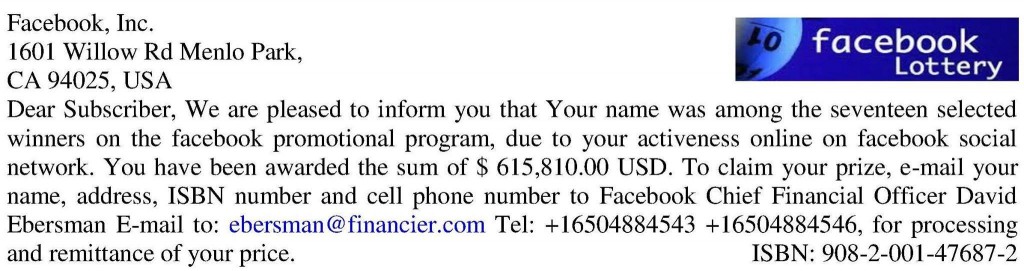
One more classic scam which never seems to get old. The lottery scam comes as an email message informing you that you won a huge amount of money and all you need to do to collect your fortune is to pay some small fees.
Lucky you! It doesn’t even matter that you don’t recall ever purchasing lottery tickets.
Since it addresses some of our wildest fantasies, such as quitting our jobs and living off the fortune for the rest of our lives, without ever having to work again, our imagination falls prey easily to images of a dreamhouse, endless summer vacations or expensive items that a normal man can only dream of.
But the dream ends as soon as you realize you have been just another scam victim.
6. Hitman scam
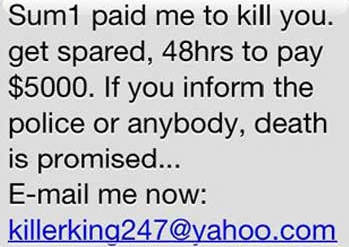
One of the most frequent scams you can meet online is the “hitman” extortion attempt. Cyber criminals will send you an email threatening you in order to obtain money.
This type of scam may come in various forms, such as the one threatening that they will kidnap a family member unless a ransom is paid in a time frame provided by the scammers.
To create the appearance of a real danger, the message is filled with details from the victim’s life, collected from an online account, a personal blog or, more and more frequently, from a social network account.
That’s why it’s not wise to offer sensitive, personal information about you on social media. It might seem like a safe and private place, where you’re only surrounded by friends, but in reality you can never know for sure who’s watching you.
That’s why sometimes it’s better to be a little bit paranoid.
7. Romance scams

How many of us have already been fooled by this one? Since this one addresses our subjective self and not our rational side, we tend to drop our guard and leave aside any logical analysis.
This scam takes place on social dating networks, like Facebook, or by sending a simple email to the potential target.
The male scammers are often located in West Africa, while the female scammers are mostly from the eastern parts of Europe.
The male scammers are often located in West Africa, while the female scammers are mostly from the eastern parts of Europe.
Cyber criminals have abused this scamming method for years by using the online dating services. They improved their approach just by testing the potential victims’ reactions.
This scheme or this game may take place for several months or more in order to gain the trust of that person. In many cases, it even goes to the moment when a meeting is arranged.
When this happens, two things may take place:
In a recent romance scam case that was mediatized, a woman lost
8. Fake antivirus software
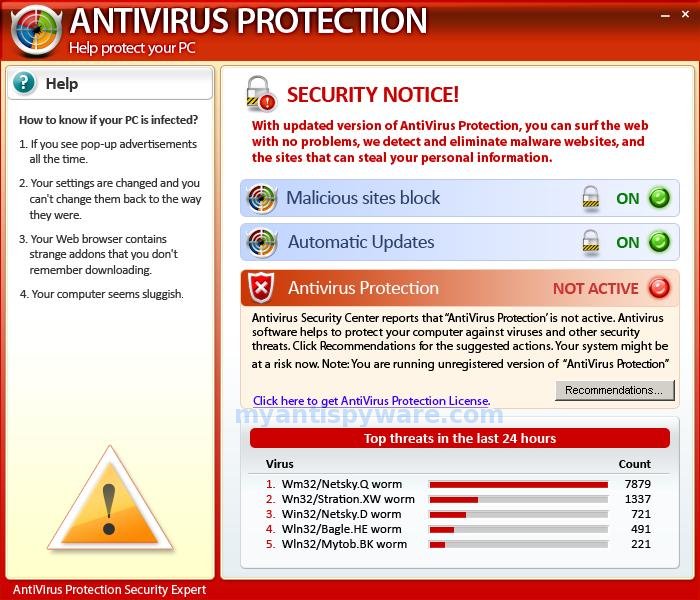
We all saw at least once this message on our screens: “You have been infected! Download antivirus X right now to protect your computer!”.
Many of these pop-ups were very well created to resemble actual messages that you might get from Windows or from a normal security product.
If you are lucky, there is nothing more than an innocent hoax that will bother you by displaying unwanted pop-ups on your screen while you browse online.
In this case, to get rid of the annoying pop-ups, we recommend scanning your system using a good antivirus product.
If you are not so lucky, you can end up with malware on your system, such as a Trojan or a keylogger.
This kind of message could also come from one of the most dangerous ransomware threats around, such as CryptoLocker, which is capable of blocking and encrypting your operating system and requesting you a sum of money in exchange for the decryption key.
To avoid this situation, we recommend using a specialized security productagainst this kind of financial malware, besides your traditional antivirus program.
9. Facebook impersonation scam (hijacked profile scam)

Facebook is today the most popular social media network. For this reason, important companies and businesses use it to communicate with customers and promote their products.
With so many friends and connections on this online platform, we use Facebook not only to check our friends’ activities and updates, but also to chat with them.
If most friends, colleagues and social connections are on Facebook, it is perfectly normal for such a place to also attract the unwanted attention of online scammers.
Just imagine your account being hacked by a cyber criminal and gaining access to your close friends and family.
Since it is so important for your privacy and online security, you should be very careful in protecting your personal online accounts just the way you protect your banking or email account. Set a double authentication method as soon as possible. This will act as an additional layer of security, besides your password.
10. Make money fast scams (Economic scams)
The following common online scam is extremely popular: cyber criminals will lure you into believing you can make easy money on the internet. They’ll promise you non-existent jobs, plans and methods of getting rich quickly and money from official government sources.
It is a quite simple and effective approach, because it simply addresses one’s basic need for money, especially when that person is in a difficult financial situation.
From this point of view, this scamming method is similar to the romance scam mentioned above, where the cyber attackers address the romantic needs of the victim.
The fraudulent posting of non-existent jobs for a variety of positions is part of the online criminals’ arsenal.
The fraudulent posting of non-existent jobs for a variety of positions is part of the online criminals’ arsenal.
Using various job types, such as work-at-home scams, the victim is lured into giving away personal information and financial data with the promise of a well paid job that will bring lots of money in a very short period of time.
11. Travel scams

These scams usually appear in the hot summer months or before the short winter vacations, for Christmas or New Year’s Day.
The scenario is usually like this: you receive an email containing an amazing offer for an extraordinary hard to get to destination (usually an exotic place) that expires in a short period of time and you must not miss.
The problem is that some of these offers actually hide some necessary costs until you pay for the initial offer. Others simply take your money without sending you anywhere.
In such cases, we suggest that you study very well the travel offer and look for hidden costs, such as: airport taxes, tickets that you need to pay to access a local attraction, check if the meals are included or not, other local transportation fees between your airport and the hotel or between the hotel and the main attractions mentioned in the initial offer, etc.
As a general rule, we suggest that you go with the trustworthy, well known travel agencies.
You can also check if by paying individually for plane tickets and for accommodation you receive the same results as in the received offer.
Conclusion
Online scams developed using increasingly sophisticated means of deceiving users, especially in the rich Western countries.
According to FBI, online scams have increased over the last 10 years and the total losses doubled in the recent years, affecting both private individuals and large scale businesses. For this reason, cyber criminal activities are now subject to federal investigations and are treated as a very serious problem that affects us all.
For an extended list of common fraud schemes discovered and analyzed by FBI, you can check this article.
You may think that you can’t be fooled by these online scams, since some of them are quite hilarious, such as the one promising to send you money or the one where the scammers pretend to be FBI agents.
But some stories are so convincing for the potential victims that it is difficult to know how to deal with them.
Since some scams are so well organized and convincing, and the people behind so difficult to catch, we need to always keep our guard up. Stay informed about the latest scamming strategies.
* This article was initially published by Aurelian Neagu in September 2014 and updated by Cristina Chipurici in May 2016.





















